1. Overview
In September 2025, a coordinated Advanced Persistent Threat (APT) campaign was discovered, targeting both Windows and macOS systems. The campaign masqueraded as legitimate software patches, including Nvidia updates, arm64-fixer, and mac_camera.driver. Through in-depth analysis, the operation has been attributed to the Lazarus Group, a North Korean state-sponsored APT actor.
Lazarus is known for conducting multifaceted cyber campaigns with diverse objectives, including financial gain (e.g., cryptocurrency theft and banking fraud), cyber espionage (targeting governments and defense contractors), and destructive attacks. Their operations commonly employ techniques such as spear-phishing, weaponized documents, watering hole attacks, custom binary deployment, and supply chain compromise. Their hallmark tactics include multi-stage C2 infrastructure, code obfuscation, and anti-analysis techniques to evade detection. International reports have linked the group to high-profile cryptocurrency heists, bank wire fraud, ransomware incidents, and data-wiping campaigns.
| OS | macOS | Windows |
|---|---|---|
| Trigger File | mac_camera.driver | run.vbs |
| Environment Setup | node.js installation | node.js installation |
| Main Script | main.js | main.js |
| Additional Payload | – | drvupdate.exe (Nukesped) |
| Persistence | drivfixer.sh | %USERPROFILE%\.n2\pay |
| Data Collected | System and browser information | System and browser information |
| Remote Command Execution | Supported | Supported |
Malware Distribution and Execution Summary
The attacker initiates execution by prompting the installation of node.js and running the main.js script, which communicates with the C2 server to download and decrypt a secondary Python-based payload. Once executed, this script collects system information, Chromium-based browser credentials, and credit card data, and exfiltrates the data to the C2 server. The agent also receives remote instructions for executing additional malicious actions.
Distribution Vectors
- The attacker distributes compressed archives or shell scripts named:
nvidiaRelease.zipmac_camera.driver- Others resembling legitimate software
- Decompressed content includes:
- A
run.vbsfile targeting Windows - A shell script
mac_camera.drivertargeting macOS
- A
Execution Flow Upon User Interaction
- Upon execution of
run.vbsormac_camera.driver,node.jsis installed andmain.jsis launched, establishing communication with the C2 server. - A supplementary archive (
p2.zip) is downloaded and extracted to enablepython.exe. node.execonnects to the C2 and triggers the execution of a Python script.- The Python script is encrypted and follows a multi-step decryption routine: string reversal → Base64 decoding → zlib decompression.
- Ultimately, sensitive data is collected and transmitted to the C2 server. The environment is configured to re-execute the Python script upon system reboot.
Data Collection and Exfiltration
The decrypted Python script collects and exfiltrates the following data:
- System Metadata: OS version, hostname, release/build number, username, UUID
- Geolocation Data: IP address, country, city, ISP, GPS coordinates, time zone
- Browser Artifacts: Chromium-based browser credentials and credit card data
Command & Control Functionality
- Upon each system reboot, the malware contacts the C2 server to retrieve and execute additional remote commands.
2. Technical Analysis
2.1 macOS Attack Flow
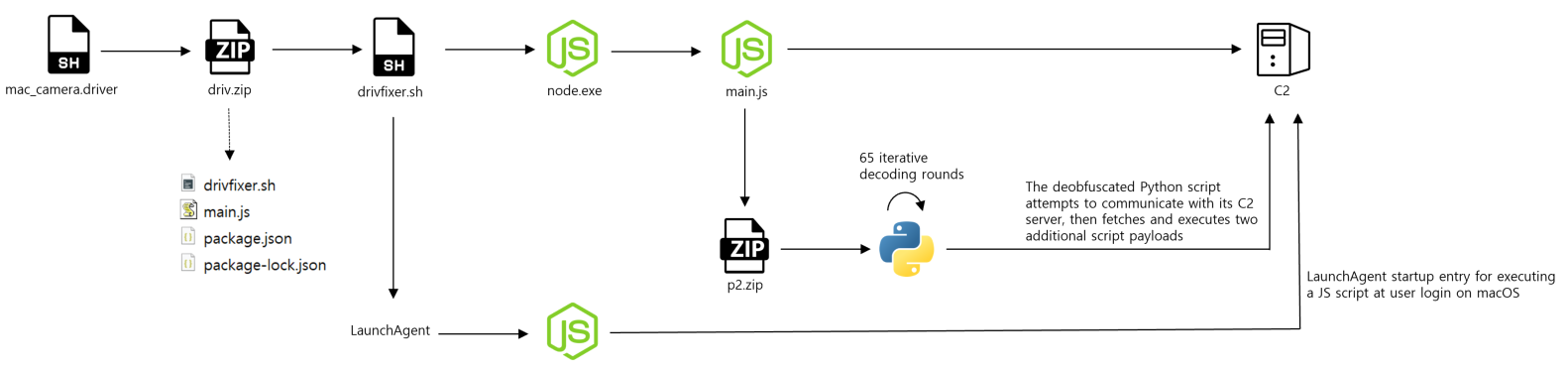

Malware Architecture Diagram (PPTX)
Execution Trigger
- Shell script disguises:
arm64-fixer,mac_camera.driver,mac_camera.driver-fix1816
Shell Script Actions
-
Downloads and extracts a compressed archive (
driv.zip) -
Executes a secondary script:
drivfixer.sh -
Installs
node.jsand executes the embeddedmain.jsfile -
Downloads additional encrypted data and executes a Python payload from the C2 server
-
Maintains persistence by registering:
-
Performs data collection and exfiltration to the C2
-
Retrieves and executes remote commands after each system reboot
Data Collected on macOS
- System Info: OS, hostname, release/version, username, UUID
- Geolocation: IP, country, city, ISP, coordinates, time zone
- Browsers: Chromium-based credentials and card data (Chrome, Brave, Opera, Yandex, Edge)
2.2 Windows Attack Flow
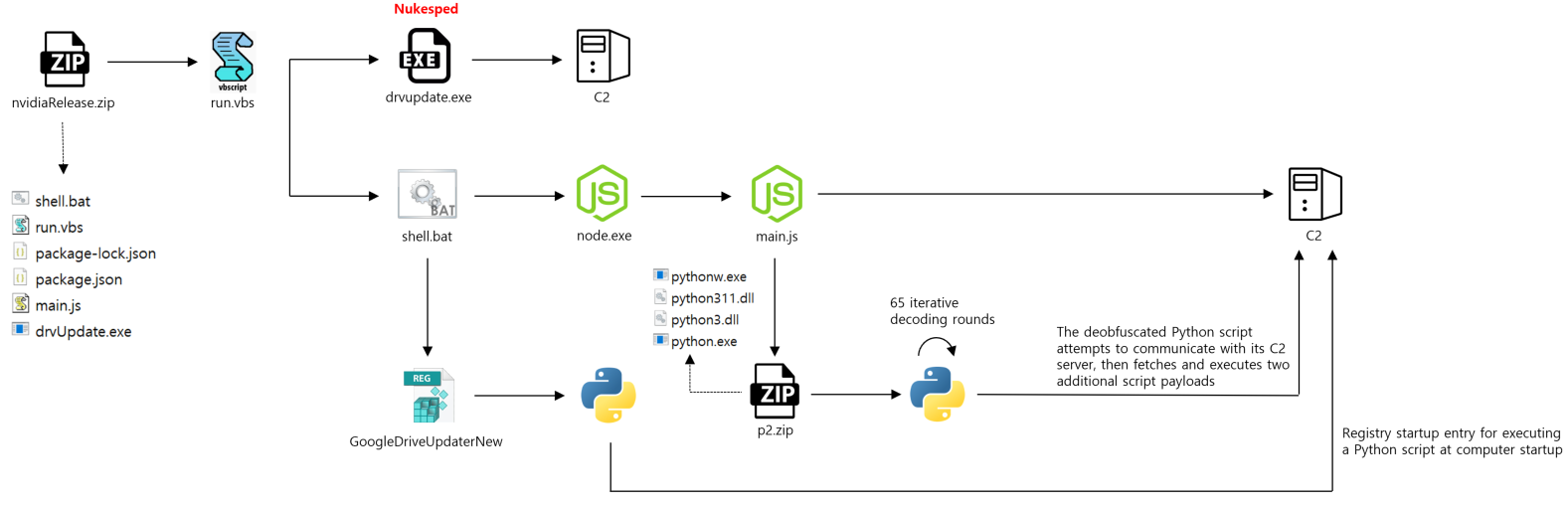

Execution Trigger
- Delivered via compressed files:
nvidiaRelease.zipnvidiaReleasenew.zipupdate93w.zip
VBS Script Behavior
-
If running on Windows 11 or later, executes
drvUpdate.exe -
Runs a batch script (
shell.bat) -
Installs
node.jsand runs the embeddedmain.js -
Downloads and executes additional Python scripts from the C2 server
-
Maintains persistence via the Windows registry:
-
Sends collected data to the C2
-
Executes new C2 commands upon each system reboot
Data Collected on Windows
- System Info: OS, hostname, release/version, username, UUID
- Geolocation: IP, country, city, ISP, coordinates, time zone
- Browsers: Chromium-based credentials and card data (Chrome, Brave, Opera, Yandex, Edge)
Behavioral Analysis of Nukesped (drvupdate.exe)
- Execution Condition: Triggers only on Windows 11 or newer
- String Decryption: Encrypted strings are decoded using Base64 + XOR 0x49
- C2 Handshake Requirement: Communication occurs only when:
- Client sends:
"ca2h6FmbGtsdw6bHJpnMzI0" - Server responds:
"Z2WtchZ4"
- Client sends:
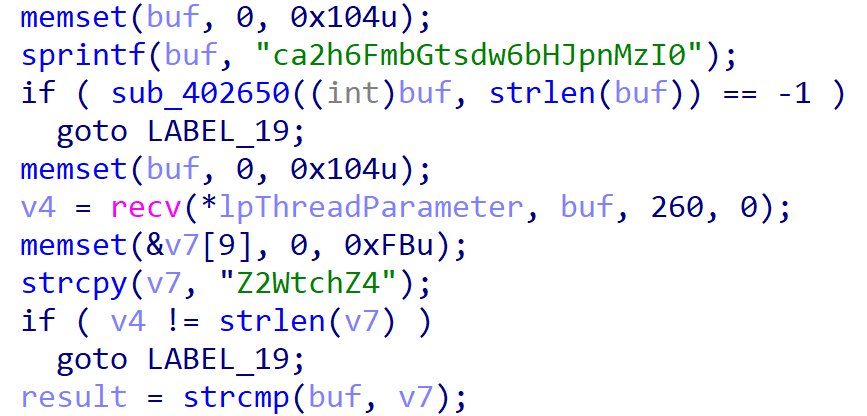

- Remote Shell Execution:
- Receives command string from the C2
- Executes using:
cmd.exe /c [command] - Output is captured, Base64-encoded, and returned via pipe to the C2
3. IoC
md5 (Files hashes contained in the downloaded ZIP archive)
f277110800d861faa6a737c8d668d297 .npl
cdf296d7404bd6193514284f021bfa54 arm64-fixer.zip
2d8c8c6323a4fea1952405f2daad5d7a browxyz2
f9e18687a38e968811b93351e9fca089 clickfix-1.bat
37911a1e8ca8a481cd989fafe7bfb75a decoded_browxyz2.bin
0b73c183056cdbacddcd5eb0d1191b3b decoded_npl.bin
858b616a388f6220e2fbcdaf545a9695 decoded_pay.bin
57a3b11361ea5908d7f79395f12e14f8 decoded_pay2.bin
0dae0f501fca7db547726c78db4ae172 driv.zip
cbd183f5e5ed7d295d83e29b62b15431 driv.zip
6175efd148a89ca61b6835c77acc7a8d drvupdate.exe
fc7b67af44b474db1bbc808a8f2a25f0 mac_camera.driver
8731b650457211decd5a7aa940dd8f0e mac_camera.driver-fix1816
b52e105bd040bda6639e958f7d9e3090 main.js
fcc0114e34b352d9d3312118c6fd9341 main.js
846b1734829ef754a42d915474b43192 nvidiaRelease (3).zip
8c274285c5f8914cdbb090d72d1720d3 nvidiaReleasenew.zip
a4e58b91531d199f268c5ea02c7bf456 nvidiarelease.zip
0550b73535fc3de5aec297707df73646 pay
3ef7717c8bcb26396fc50ed92e812d13 run.vbs
09d2336c6b76fa499f52773d930788a4 run.vbs
983a8a6f4d0a8c887536f5787a6b01a2 shell.bat
6559d05cfcf294ef325a3eb772c3d3ba update92w.zip
5a20eb4497913196212601430bd8da9d update93w.zip
13400d5c844b7ab9aacc81822b1e7f02 arm64-fixer\drivfixer.sh
b52e105bd040bda6639e958f7d9e3090 arm64-fixer\main.js
13400d5c844b7ab9aacc81822b1e7f02 driv\drivfixer.sh
ef7b96bffe252ede8259fea30fc3a9a3 driv\main.js
13400d5c844b7ab9aacc81822b1e7f02 drivv\drivfixer.sh
15e48aef2e26f2367e5002e6c3148e1f drivv\main.js
6175efd148a89ca61b6835c77acc7a8d nvidiarelease\drvUpdate.exe
b52e105bd040bda6639e958f7d9e3090 nvidiarelease\main.js
3ef7717c8bcb26396fc50ed92e812d13 nvidiarelease\run.vbs
983a8a6f4d0a8c887536f5787a6b01a2 nvidiarelease\shell.bat
6175efd148a89ca61b6835c77acc7a8d nvidiaRelease (3)\drvUpdate.exe
b52e105bd040bda6639e958f7d9e3090 nvidiaRelease (3)\main.js
945acbf53bd61ee1d6475c47f1db15d8 nvidiaRelease (3)\run.vbs
8e8066fa5de1b8cad438c2323bdf2304 nvidiaRelease (3)\shell.bat
6175efd148a89ca61b6835c77acc7a8d nvidiaReleasenew\drvUpdate.exe
15e48aef2e26f2367e5002e6c3148e1f nvidiaReleasenew\main.js
3ef7717c8bcb26396fc50ed92e812d13 nvidiaReleasenew\run.vbs
983a8a6f4d0a8c887536f5787a6b01a2 nvidiaReleasenew\shell.bat
fcc0114e34b352d9d3312118c6fd9341 update92w\main.js
09d2336c6b76fa499f52773d930788a4 update92w\run.vbs
983a8a6f4d0a8c887536f5787a6b01a2 update92w\shell.bat
ef7b96bffe252ede8259fea30fc3a9a3 update93w\main.js
09d2336c6b76fa499f52773d930788a4 update93w\run.vbs
983a8a6f4d0a8c887536f5787a6b01a2 update93w\shell.bat
C2
avalabs-digital.store
driverservices.store
webmail.driverservices.store
www.driverservices.store
block-digital.online
cpanel.block-digital.online
webmail.block-digital.online
www.block-digital.online
69.10.53.86
141.98.168.79
198.54.116.177
103.231.75.101
45.89.53.54
199.188.200.147
198.54.119.94
192.64.119.25
45.159.248.110
http://69.10.53.86
http://141.98.168.79
https://block-digital.online/drivers/mac_camera.driver-fix1816
http://block-digital.online/drivers/mac_camera.driver-fix1816
https://block-digital.online/drivers/mac_camera.driver
https://block-digital.online/drivers/camera
http://block-digital.online/
https://www.block-digital.online/
https://block-digital.online/
https://block-digital.online/drivers/cam_driver
http://block-digital.online/drivers/cam_driver
https://block-digital.online/drivers/
http://block-digital.online/cpanel
https://block-digital.online/drive
https://driverservices.store/visiodrive/arm64-fixernew
http://avalabs-digital.store/update/update93w
https://avalabs-digital.store/update/update93w
http://avalabs-digital.store/
http://avalabs-digital.store/cpanel
https://avalabs-digital.store/update/update93w/
https://avalabs-digital.store/update/z-update93m
https://driverservices.store/visiodrive/nvidiaReleasenew.zip
https://driverservices.store/visiodrive/nvidiaRelease.zi
http://driverservices.store/
https://driverservices.store/
https://driverservices.store/visiodrive/nvidiaRelease.zip
https://driverservices.store/visiodri
https://driverservices.store/visiodrive/nvidiaRelease.zip
http://driverservices.store/visiodrive/arm64-fixernew
http://webmail.driverservices.store/
https://www.driverservices.store:2096/
https://webmail.driverservices.store/
https://driverservices.store/visiodrive/nvidiareleasenew.zip
http://driverservices.store/visiodrive
https://driverservices.store/visiodrive/nvidiarelease.zip
https://driverservices.store/visiodrive/mac-v-j1721.fixer
https://driverservices.store/visiodrive/
https://driverservices.store/visiodrive/arm64-fixer
http://driverservices.store/visiodrive/nvidiaRelease.zip
http://www.driverservices.store/



